Understanding Privacy and Security
We take the security, privacy and date protection very seriously across all of our software products. Discover some of the steps we take to make sure you are protected.
The steps we take to protect you
Cloud based software
Our cloud-based software ensures that data is regularly backed up without requiring manual intervention.
2-Factor Authentication
For software containing sensitive information, 2FA provides an extra safeguard, ensuring that unauthorized individuals cannot access this data.
Data protection
Robust data encryption ensures that sensitive information is protected from unauthorized access.
Regular testing for security vulnerabilities
Software dependencies are actively monitored for known security vulnerabilities using third party vulnerability management software.
Privacy & Security FAQ’s
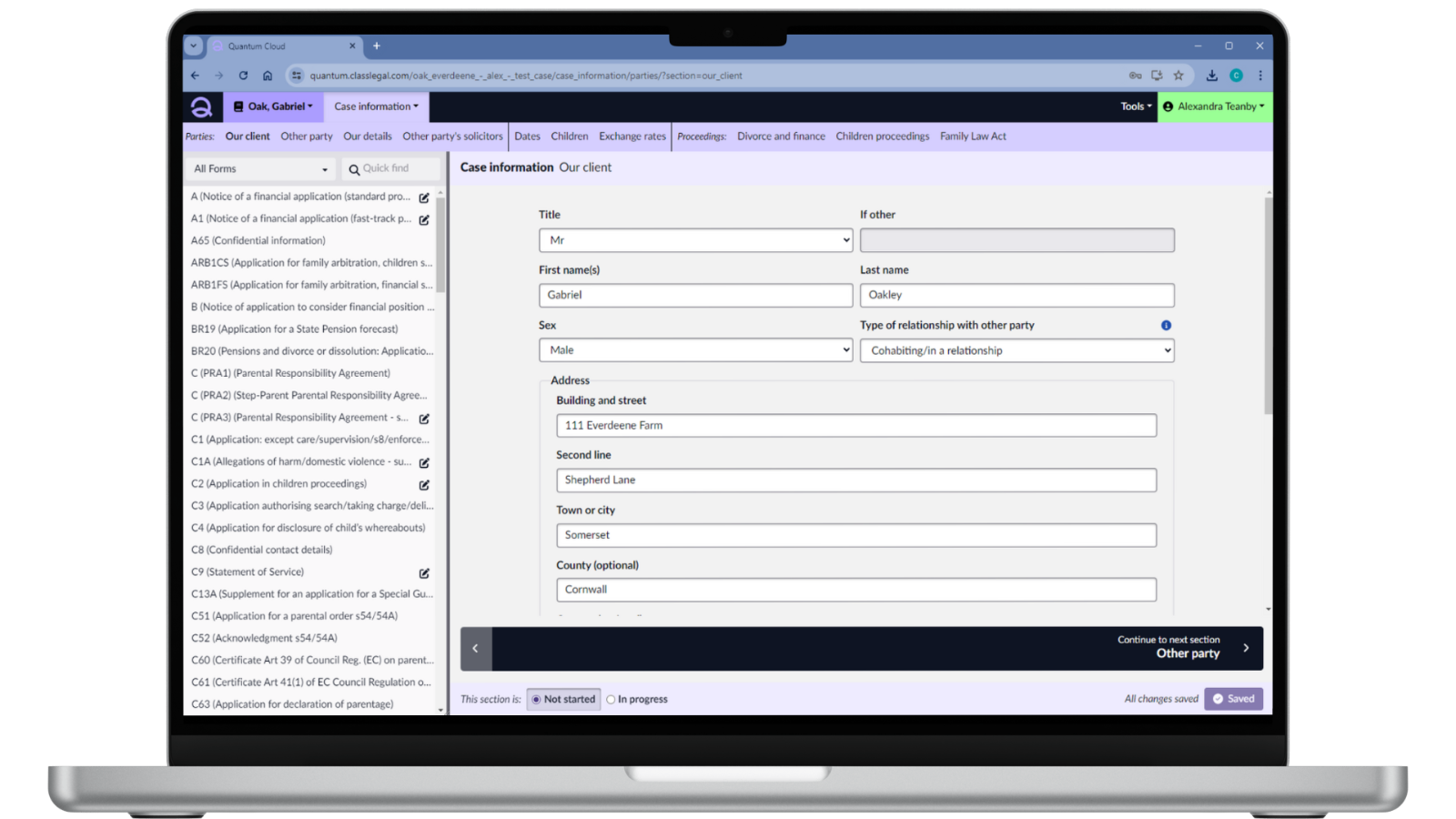
What is cloud-based software?
Cloud-based software, also known as Software as a Service (SaaS), refers to applications and services that are hosted on remote servers and accessed over the internet. Unlike traditional software, which is installed on individual computers or local servers, cloud-based software is delivered through a web browser or a dedicated client, allowing users to access it from anywhere with an internet connection.
How do you handle client data?
All data is encrypted with Transport Layer Security (TLS) version 1.2. Less secure versions of TLS will be rejected.
Amazon Cognito is used together with AWS key management Service KWS. Access to the KMS key is provided only to users. No other users including administrative users are authorised to decrypt confidential information.
Is the software regularly tested for security vulnerabilities?
Yes, software dependencies are actively monitored for known security vulnerabilities using third party vulnerability management software. Known vulnerabilities are regularly triaged and updated as necessary. The applications are penetration tested by a third party on a quarterly basis and the results are reviewed and remediated as necessary.
In which country is my data held?
All data is held in the UK and all processing is conducted within the UK, to meet GDPR rules and regulations.
Can I request security documentation?
Yes, we have some security documentation available to download from our website but if you would like any further information, please call our office on 01652 652 222 or email info@classlegal.com.
Additional security documentation
AAG Cloud Security
50.5 kb
Capitalise II - IT FAQS
536 KB
Quantum End User - Security and Compliance
85.1 kb